NetHack
From Wikipedia, the free encyclopedia
| NetHack | |
|---|---|
 A released djinni grants the player a wish. |
|
| Developer(s) | The NetHack DevTeam |
| Writer(s) | Eric S. Raymond (NetHack Guidebook)[1] |
| License | NetHack General Public License |
| Version | 3.4.3 (8 December 2003) 3.4.1 (23 February 2003) 3.4.0 (20 March 2002) 3.3 (10 December 1999) |
| Platform(s) | Cross-platform |
| Release date(s) | 1.3d (July 1987)[2] |
| Genre(s) | Roguelike |
| Input methods | Keyboard and mouse |
NetHack is a single-player roguelike video game originally released in 1987. It is a descendant of an earlier game called Hack (1985), which is a descendant of Rogue (1980).[3]
The "net" element references that its development has been coordinated through the Internet.[4] The "hack" element refers to a genre of role-playing games known as hack and slash for their focus on combat. The player takes the part of a dungeon-delving character in search of the Amulet of Yendor.[5]
Contents |
[edit] History and development
NetHack is open source and remains one of the oldest computer games still actively developed,[6] with new features and bug fixes added by a loose but secretive group of volunteers, commonly called the DevTeam. The DevTeam rarely discusses versions under development in public, and releases new versions without notice. However, they do maintain a list of known bugs. Since NetHack is open source, others are free to release patches to the game between official, versioned releases.
[edit] Gameplay
Before playing a game, the player is asked to name his or her character and then select a race, role, gender, and alignment, or allow the game to assign them. There are traditional fantasy roles such as knight, barbarian, wizard, rogue, valkyrie, monk, and samurai, but there are also unusual ones, including archaeologist, tourist, and caveman. The player character's role and alignment dictate which deity the character serves in the game.
After the player character is created, the main objective is introduced. To win the game, the player must retrieve the Amulet of Yendor, found at the lowest level of the dungeon, and sacrifice it to his or her deity. Successful completion of this task rewards the player with the gift of immortality, and the player is said to "ascend", attaining the status of demigod. In addition, a number of sub-quests must be completed, including one class-specific quest.
The player's character is usually accompanied by a pet animal, typically a kitten or little dog, although knights begin with a saddled pony. Most of the other monsters may also be tamed using magic or tempting food.
[edit] Dungeon levels
NetHack's dungeon spans about 50 levels, of which most are randomly generated when the player character first encounters them. A typical level contains a way "up" and a way "down" (these may be stairways, ladders, trapdoors etc.), along with several "rooms" joined by corridors that may contain features such as altars, shops, fountains, traps, and even sinks. Some "special" levels are of fixed design in every game session. There are several dungeon branches, including a Sokoban puzzle and Vlad's Tower.
[edit] Items and tools
NetHack features a variety of items: weapons (either ranged or melee), armor to protect the player; scrolls and spellbooks to cast; potions to quaff; and an assortment of tools such as keys and lamps.
One important aspect of NetHack's gameplay is the identification of items. For example, a newly-discovered potion may be referred to as a 'pink potion' with no other clues as to its identity. Players can perform a variety of actions and tricks to deduce, or at least narrow down, the identity of the potion. The most obvious is the somewhat risky tactic of simply drinking it.
Unlike some other roguelikes, all items of a certain type will have the same description; e.g., all scrolls of enchant weapon may be labeled 'TEMOV', and once one has been identified, all scrolls of enchant weapon found will be labeled unambiguously as such. Starting a new game will scramble the items' descriptions again, so the 'silver ring' that is a ring of levitation in one game might be a ring of hunger in another.
[edit] Blessings and curses
As in many other roguelike games, all items in NetHack are either "blessed", "uncursed", or "cursed". The majority of items are found uncursed, but the "BUC" (Blessed/Uncursed/Cursed) status of an item is unknown until it is identified or detected through other means.
Generally, a blessed item will be more powerful than an uncursed item, and a cursed item will be less powerful. Regarding objects which bestow effects upon the character, a curse will generally make the effect (more) harmful. There are exceptions, however, which are usually very specific (e.g. the cursed potion of gain level will make the character rise through the ceiling to the level above).
[edit] Character death
Like roguelikes in general, NetHack features permadeath: expired characters cannot be revived without having made backup copies of the actual save files. Players sometimes use the acronyms "YAAD" and "YASD" when discussing their characters' deaths, meaning "Yet Another Annoying Death" or "Yet Another Stupid Death". An "annoying" death is typically one that was the fault of misfortune more than the player (such as falling into a spiked, poisoned pit trap early in the game); a "stupid" death is when player's actions were directly responsible for their own death.
The prompt "Do you want your possessions identified?" (abbreviated as "DYWYPI" and used to suggest character death) is given by default at the end of any game, allowing the player to learn any unknown properties of the items found during the game.
The game sporadically saves a level on which a character has died and then integrates that level into a later game. This is done via "bones files", which are saved on the computer hosting the game. A player using a publicly-hosted copy of the game can thus encounter the remains of many other players. Players can also swap bones files via programs like Hearse.[7]
Bugs, humorous messages, stories, experiences, and ideas for the next version are discussed on the Usenet newsgroup rec.games.roguelike.nethack.[8]
[edit] Conducts
Although NetHack can be completed by new or intermediate players without any artificial limitations, experienced players often attempt "conducts" for an additional challenge. These are voluntary restrictions on actions taken, such as using no wishes, following a vegetarian or even vegan diet, or even killing no monsters. While in general conducts are tracked by the game and are displayed at death or ascension, unofficial conducts, such as the Zen conduct (in which the player's character wears a blindfold throughout the whole game), also exist within the NetHack community.
[edit] Spoilers
NetHack is largely based on discovering secrets and tricks during gameplay. It can take years for one to become well-versed in them, and even experienced players routinely discover new ones. A number of NetHack fansites and discussion forums offer lists of game secrets known as "spoilers". Many play without recourse to spoilers and regard their usage as cheating. Fans of NetHack consider an ascension without having read spoilers very prestigious; the achievement is so difficult that some question whether it has been or can be accomplished.
[edit] Interface
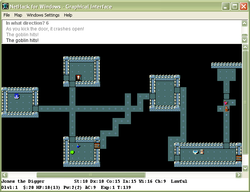
NetHack was originally created without a graphical user interface, although the option to play using one was added later in its development. Interface elements — environment, entities, and objects — are represented by arrangements of ASCII or Extended ASCII glyphs used in plain text, "DEC graphics" or "IBM graphics" mode. In addition to the environment, the interface also displays character and situational information.
A detailed example:
You see here a silver ring.
------------
##....._.....|
|...........# ------
#...........| |....|
--------------- ###------------ |...(|
|..%...........|########## ###-@...|
|...%...........### # ## |....|
+.......<......| ### ### |..!.|
--------------- # # ------
### ###
# #
---.----- ###
|.......| #
|........####
|.......|
|.......|
---------
Hacker the Conjurer St:11 Dx:13 Co:12 In:11 Wi:18 Ch:11 Lawful
Dlvl:3 $:120 HP:39(41) Pw:36(36) AC:6 Exp:5 T:1073
|
The player (The '@' sign, a wizard in this case) has entered the level via the stairs (the '<' sign) and killed a few monsters, leaving their corpses (the '%' signs) behind. Exploring, the wizard has uncovered three rooms joined by corridors (the '#' signs): one with an altar (the '_' sign), another empty, and the final one (that the wizard is currently in) containing a potion (the '!' sign), chest (the '(' sign), and has just moved onto a square containing a silver ring. Large parts of the level remain unexplored (probably to the west through the door (the '+' sign)) and the player has yet to find the down-stairs (a '>' sign) to the next level.
Apart from the original termcap interface shown above, there are interfaces that replace standard screen representations with two-dimensional images, or tiles, collectively known as "tiles mode". Graphic interfaces of this kind utilize the X Window System, the similar Microsoft Windows GUI, the Qt toolkit, or the GNOME libraries.
Enhanced graphical options also exist, such as the isometric perspective of Falcon's Eye and Vulture's Eye, or the three-dimensional rendering that noegnud offers. Vulture's Eye is a fork of the now defunct Falcon's Eye project. Vulture's Eye adds additional graphics, sounds, bugfixes and performance enhancements and is under active development in an open collaborative environment.
[edit] IRC
Nethack has an IRC channel named #nethack on the server, Freenode. Many people discuss the game there and with the resident announcer "Rodney" telling every death and announcing full moons, very little is missed.
[edit] Ports and variants
Unofficial ports exist for the Nintendo DS,[9][10] PlayStation Portable,[11] Tapwave Zodiac,[12] GP2X,[13] Windows Mobile,[14] Nokia Internet Tablets N770, N800 and up,[15][16] and Apple's iPhone and iPod touch.[citation needed]
Slash'EM[17] and SporkHack[18] are actively developed variants.
[edit] References
- ^ Raymond, Eric S. (2003-12-08). "A Guide to the Mazes of Menace (Guidebook of Nethack)". NetHack.org. http://www.nethack.org/v343/Guidebook.html. Retrieved on 2008-12-15.
- ^ "NetHack 1.3d". Wikihack. http://nethack.wikia.com/wiki/NetHack_1.3d. Retrieved on 2008-12-15.
- ^ Au, Wagner James (2000-01-27). "The Best Game Ever". Salon.com. http://www.salon.com/tech/feature/2000/01/27/nethack/. Retrieved on 2008-12-15. "Rogue became the basis for an offspring called Hack, and in acknowledgement of code fixes and additions passed back and forth via Usenet, the quickly evolving game was renamed Nethack [sic].".
- ^ "NetHack 3.4.3: Information". NetHack.org. http://www.nethack.org/common/info.html. Retrieved on 2008-12-15.
- ^ Au, Wagner James (Aug 1997), "Back to the Dungeon", Wired, http://www.wired.com/wired/archive/5.08/streetcred.html?pg=3
- ^ Eli (2006-07-16). "NetHack". Jay Is Games. http://jayisgames.com/archives/2006/07/nethack.php. Retrieved on 2008-12-15.
- ^ "Hearse". http://hearse.krollmark.com/. Retrieved on 2008-12-15.
- ^ "rec.games.roguelike.nethack". Wikihack. http://nethack.wikia.com/wiki/rec.games.roguelike.nethack. Retrieved on 2008-12-15.
- ^ Pernsteiner, Stuart (2007-03-17). "NetHack for the Nintendo DS". Stuart Pernsteiner's Website. http://stuartp.commixus.com/nhds/. Retrieved on 2008-12-15.
- ^ Kosinski, Brett (2008-10-19). "NetHackDS". The "B" Ark. http://frodo.dyn.gno.org/~brettk/NetHackDS. Retrieved on 2008-12-15.
- ^ "Porting NetHack to the PSP - Latest news". 2007-03-22. http://www.feelthepawa.com/PSP/NetHack/. Retrieved on 2008-12-15.
- ^ "NetHack and SlashEM for Palm OS". Retrobits.net. http://www.retrobits.net/palmos/nethack.shtml. Retrieved on 2008-12-15.
- ^ "Nethack (graphical)". GP2X Wiki. 2008-07-12. http://wiki.gp2x.org/wiki/Nethack_(graphical). Retrieved on 2008-12-15.
- ^ "Download NetHack 3.4.3 for Windows Mobile PocketPC - Softpedia". Softpedia. 2006-04-16. http://handheld.softpedia.com/get/Games/Adventure/NetHack-9837.shtml. Retrieved on 2008-12-13.
- ^ Caron, Frank (2007-05-24). "The N800 surfs nicely, but how does it game?". Ars Technica. http://arstechnica.com/journals/thumbs.ars/2007/05/24/n800-gaming-overview. Retrieved on 2008-12-15.
- ^ "Nethack ported to Maemo on Nokia 770". http://www.rengels.de/computer/nethack/.
- ^ "The Slash'EM Homepage". http://slashem.sourceforge.net/.
- ^ "SporkHack". http://www.sporkhack.com.
[edit] External links
| Wikiquote has a collection of quotations related to: NetHack |
- NetHack Official Site
- NetHack at the Open Directory Project
- NetHack at MobyGames
- Hall of Fame - NetHack at GameSpy
- Public NetHack server
- SporkHack Official Site
- Archive of NetHack MS-DOS executables
- Vulture's Eye project homepage
- #nethack on FreeNode
Wikis
- NetHack on Wikihack, an external wiki
- NetHack guide at StrategyWiki