DeCSS
From Wikipedia, the free encyclopedia
| This article's introduction section may not adequately summarize its contents. To comply with Wikipedia's lead section guidelines, please consider expanding the lead to provide an accessible overview of the article's key points. |
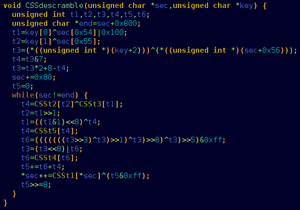
DeCSS is a computer program capable of decrypting content on a DVD-Video disc encrypted using the Content-Scrambling System (CSS).
Contents |
[edit] Origins and history
DeCSS was devised by three people, two of whom remain anonymous. It was released on the Internet mailing list LiViD in October 1999. The one known author of the trio is Norwegian programmer Jon Lech Johansen, whose home was raided in 2000 by Norwegian police. Still a teenager at the time, he was put on trial in a Norwegian court for violating Norwegian Criminal Code section 145[1], and faced a possible jail sentence of two years and large fines, but was acquitted of all charges in early 2003. However, on March 5, 2003, a Norwegian appeals court ruled that Johansen would have to be retried. The court said that arguments filed by the prosecutor and additional evidence merited another trial. On December 22, 2003, the appeals court agreed with the acquittal, and on January 5, 2004, Norway's Økokrim (Economic Crime Unit) decided not to pursue the case further.
The program was first released on October 6, 1999 when Johansen posted an announcement of DeCSS 1.1b, a closed source Windows-only application for DVD ripping, on the livid-dev mailing list. The source code was leaked before the end of the month. The first release of DeCSS was preceded by a few weeks by a program called DoD DVD Speed Ripper[2] from a group called Drink or Die, which didn't include source code and which apparently did not work with all DVDs. Drink or Die reportedly disassembled the object code of the Xing DVD player to obtain a player key. The group that wrote DeCSS, including Johansen, came to call themselves Masters of Reverse Engineering and may have obtained information from Drink or Die.[2]
The CSS decryption source code used in DeCSS was mailed to Derek Fawcus before DeCSS was released. When the DeCSS source code was leaked, Fawcus noticed that DeCSS included his css-auth code in violation of the GNU GPL. When Johansen was made aware of this, he contacted Fawcus to solve the issue and was granted a license to use the code in DeCSS under non-GPL terms.
Johansen was involved in a flamewar with another member on livid-dev over the GPL violation issue. Johansen was a FreeBSD supporter and criticized Linux. The main point of the dispute was that Johansen claimed that he had been granted a non-GPL license by Fawcus for the css-auth code, while the other party claimed that he was lying. The flamewar ended when Fawcus confirmed Johansen's side of the story.[3] At the end of 2000, a document written by an anonymous author surfaced on the Internet.[4] It accuses Johansen of lying, slandering Linux and violating the GPL. One of the document's claims is that UDF support was not an issue under Linux. This is disputed by Matthew Pavlovich, LiViD project leader, who testified in Universal v. Reimerdes that UDF under Linux was an issue.[5]
On January 22, 2004, the DVD CCA dropped the case against Jon Johansen.[6]
[edit] Jon Lech Johansen's involvement
The DeCSS program was a collaborative project, in which Jon wrote the Graphical User Interface. The transcripts from the Borgarting Court of Appeal, published in the Norwegian newspaper VG, contain the following description of the process which led to the release of DeCSS:[7]
Through Internet Relay Chat (henceforth IRC), [Jon Lech Johansen] made contact with like-minded [people seeking to develop a DVD-player under the Linux operating system]. 11 September 1999, he had a conversation with "mdx" about how the encryption algorithm in CSS could be found, by using a poorly secured software-based DVD-player. In a conversation [between Jon Lech Johansen and "mdx"] 22 September, "mdx" informs that "the nomad" had found the code for CSS decryption, and that "mdx" now would send this [code] to Jon Lech Johansen. "The nomad" allegedly found this decryption algorithm through so-called reverse engineering of a Xing DVD-player, where the [decryption] keys were more or less openly accessible. Through this, information that made it possible [for "mdx"] to create the code CSS_scramble.cpp was retrieved. From chat logs dated 4 November 1999 and 25 November 1999, it appears that "the nomad" carried through the reverse engineering process on a Xing player, which he characterized as illegal. As the case is presented for the High Court, this was not known by Jon Lech Johansen before 4 November [1999]. Regarding the authentication code, the High Court takes for its basis that "the nomad" obtained this code through the electronic mailing list LiVid (Linux Video) on the internet, and that it was created by Derek Fawcus. It appears through a LiVid posting dated 6 October 1999 that Derek Fawcus on this date read through the DeCSS source code and compared it with his own. Further, it appears that "the creators [of DeCSS] have taken [Derek Fawcus' code] almost verbatim - the only alteration was the removal of [Derek Fawcus'] copyright header and a paragraph containing commentaries, and a change of the function names." The name [of the code] was CSS_auth.cpp. The High Court takes for its basis that the program Jon Lech Johansen later programmed, the graphical user interface, consisted of "the nomad's" decryption algorithm and Derek Fawcus' authentication package. The creation of a graphical user interface made the program accessible, also for users without special knowledge in programming. The program was published on the internet for the first time 6 October 1999, after Jon Lech Johansen had tested it on the movie "The Matrix." In this, he downloaded approximately 2.5%. 200 megabytes, of the movie to the hard drive on his computer. This file is the only film fragment Jon Lech Johansen has saved on his computer.
[edit] Technology and derived works
When the release of the DeCSS source code made the CSS algorithm available for public scrutiny, it was soon found to be susceptible to a brute force attack quite different from DeCSS. The encryption is only 40-bit, and does not use all keys; a high-end home computer in 1999 running optimized code could brute-force it within 24 hours, modern computers can now brute-force it in a few seconds or less.
Programmers around the world created hundreds of programs equivalent to DeCSS, some merely to demonstrate the trivial ease with which the system could be bypassed, and others to add DVD support to open source movie players. The licensing restrictions on CSS make it impossible to create an open source implementation through official channels, and closed source drivers are unavailable for some operating systems, so some users need DeCSS to watch movies.
In early 2000, a program with the same name but a very different purpose (removing Cascading Style Sheets tags from HTML code) was also developed. People were encouraged to mirror the website of this unrelated program, as a means of presumably making it more difficult for anti-DeCSS agents to find the 'real' DeCSS program.[8]
[edit] Legal response
The chief complaint against DeCSS (and similar programs) is that once the unencrypted source video is available in digital form, it can be copied without degradation, so DeCSS can be used for copyright infringement. However, lossless digital image copying of DVDs without decrypting them was already widespread before DeCSS, especially in East Asia.[citation needed] Furthermore, various DVD backup utilities that made use of "licensed" CSS decoding routines were also widely available.
In protest against legislation that prohibits publication of copy protection circumvention code in countries that implement the WIPO Copyright Treaty (such as the United States' Digital Millennium Copyright Act), some have devised clever ways of distributing descriptions of the DeCSS algorithm, such as through steganography, through various Internet protocols, on t-shirts and in dramatic readings, as MIDI files, as a series of haiku poems,[9] and even as a so-called illegal prime number. However, the CSS algorithm seems to require more characters to describe in a computer programming language than the RC4 algorithm by RSA Data Security; one of the shortest implementations of DeCSS (called "efdtt") is 434 bytes. Because of this, it has not been distributed by some of the more "inventive" methods used to distribute the RSA algorithm during the days of ITAR — it is not suitable for tattoos, email signatures, etc.
The first legal threats against sites hosting DeCSS, and the beginning of the DeCSS mirroring campaign, began in about early November 1999 (Universal v. Reimerdes). As a response to these threats a program also called DeCSS but with an unrelated function was developed. This program can be used for stripping Cascading Style Sheets tags from an HTML page. In one case, a school removed a student's webpage that included a copy of this program, mistaking it for the original DeCSS program, and received a great deal of negative media attention. The CSS stripping program had been specifically created to bait the MPAA in this manner.[10]
As of 2007, DeCSS and several clones (which have not been specifically brought to court) can be readily obtained over the Internet.
[edit] External links
- Gallery of CSS Descramblers (David S. Touretzky)
- DeCSS Central - Information about DVD, CSS, DeCSS, LiVid, the DVD CCA and MPAA and the various lawsuits surrounding DeCSS.
- 2600 News: DVD Industry Takes 2600 to Court
- Aftenposten: Prosecutors let DVD-Jon's victory stand
- The Openlaw DVD/DeCSS Forum Frequently Asked Questions (FAQ) List
- DeCSS Haiku - How to decrypt a DVD - in Haiku form - by Seth Schoen
- The history of the DeCSS Haiku, by Seth Schoen
- 42 ways to distribute DeCSS
- DeCSS Explained - A technical overview of the CSS decryption algorithm.
- DeCSS.c, The DeCSS source code
- The Truth about DVD CSS cracking by MoRE and {dEZZY/DoD}
[edit] References
- ^ "Norwegian Criminal Code section 135-147". http://www.lovdata.no/all/tl-19020522-010-017.html. Retrieved on July 31 2008.
- ^ a b "The Truth about DVD CSS cracking; November 4, 1999". http://www.lemuria.org/DeCSS/dvdtruth.txt. Retrieved on January 4 2007.
- ^ "Derek Fawcus ending liviv-dev flamewar by confirming Johansen's side of the story". http://web.archive.org/web/20001202051300/http://livid.on.openprojects.net/pipermail/livid-dev/1999-October/000548.html.
- ^ "http://www.trust-us.ch/decss/decsstruth.txt". http://www.trust-us.ch/decss/decsstruth.txt. Retrieved on December 5 2005.
- ^ "Transcript of Trial - Day 5, MPAA v. 2600 NY; July 21, 2000". http://www.eff.org/IP/Video/MPAA_DVD_cases/20000721_ny_trial_transcript.html. Retrieved on December 5 2005.
- ^ "EFF: DVD Descrambling Code Not a Trade Secret". http://www.eff.org/IP/Video/DVDCCA_case/20040122_eff_pr.php. Retrieved on December 5 2005.
- ^ Hele DVD-dommen
- ^ http://www.pigdog.org/decss/
- ^ "http://www-2.cs.cmu.edu/~dst/DeCSS/Gallery/decss-haiku.txt". http://www-2.cs.cmu.edu/~dst/DeCSS/Gallery/decss-haiku.txt. Retrieved on December 5 2005.
- ^ "Pigdog Journal - DeCSS Distribution Center". http://www.pigdog.org/decss/. Retrieved on May 28 2007.

